基本的に AWS を利用する際は GUI(グラフィカルインタフェース、Web の管理画面)から利用するケースが多いと思います。
しかし数が多くなってくると、GUI(Web の管理画面)からの操作ではミスが多くなったり作業に時間が掛かるようになります。
(1台、2台程度なら GUI から操作する方が効率がいいですが)
そのため AWS では、AWS CLI(コマンドライン)が用意されており、AWS CLI を利用することでセキュリティグループの作成やセキュリティグループのルールの追加、EC2 インスタンスの作成をすることができます。
実際に AWS 環境で構築や運用をすると、大量に EC2 インスタンスを作成する場合は GUI(Web の管理画面)から 1つ 1つボタンをクリックして作成するより、AWS CLI(コマンドライン)から実行した方が短時間で正確に大量の EC2 インスタンスを作成することが可能になります。
そこで今回は AWS CLI(コマンドライン)でセキュリティグループと EC2 インスタンスを作成する手順を解説します。
【AWS】AWS CLI(AWS コマンドライン)からの EC2 インスタンス作成手順
【AWS】aws(AWS CLI) & jq コマンドの便利な使い方解説【運用管理に役立つ】
【AWS】【Windows&Linux】「EC2 インスタンス」または「パソコン」に AWS CLI(aws コマンド)及び jq コマンドをインストールする手順
AWS CLI より EC2 インスタンスを作成するための手順概要
- セキュリティグループの作成(create-security-group)
- セキュリティグループにルールを追加する(インバウンド、authorize-security-group-ingress)
- セキュリティグループにルールを追加する(アウトバウンド、authorize-security-group-egress)
- アウトバウンド全て許可の設定を削除する(アウトバウンドを設定した場合に必要)
- AMI、セキュリティグループを指定して EC2 インスタンスを作成する
それぞれで作成状況を確認しつつ作業を進めます。
セキュリティグループの作成(create-security-group)
最初にセキュリティグループを作成します。
■1行で終わらせる場合
|
$ aws ec2 create-security-group –group-name Test-EC2-Instance-001-sg –vpc-id vpc-xxxxxx –description “Test EC2 Instance 001 by AWS CLI” |
■複数行で実行する場合
|
$ aws ec2 create-security-group \ –group-name Test-EC2-Instance-001-sg \ –vpc-id vpc-xxxxxx \ –description “Test EC2 Instance 001 by AWS CLI” |
各行末にバックスラッシュ(\、円マーク)を置くことでコマンドの途中で改行することができます。
バックスラッシュを置くことでコマンドが見やすくなるというメリットがあります。
ただし個人的には大量の EC2 インスタンスを作成することを考慮すると 1行 1コマンドを推奨します。(今回の記事では1行コマンドを中心に解説します)
例えば、Excel でコマンド管理をすることでコマンドのミスを減らすことが出来るようになります。
セキュリティグループを一気に大量に作成する場合
1行 1コマンドの場合は、以下のような感じになります。
■コマンド
|
aws ec2 create-security-group –group-name Test-EC2-Instance-001-sg –vpc-id vpc-xxxxxxxxxx –description ” Test-EC2-Instance-001″ |
■コマンド実行結果
以下のような感じでコマンドの実行結果の返り値で「GroupId」が返ってきます。
※ただしコマンドラインで何度も作成・削除を繰り返すため GroupId は使わないコマンドにしています。
|
[ec2-user@RedHat8 ~]$ aws ec2 create-security-group –group-name Test-EC2-Instance-001-sg –vpc-id vpc-xxxxxxxxxx –description ” Test-EC2-Instance-001″ |
■AWS 管理画面
create-security-group でセキュリティグループを作成する際にタグ付けはできない
ちなみに aws ec2 create-security-group でセキュリティグループを作成する際にタグ付けはできません。
(オプションがありません)
タグを付けたい場合は、別途「aws ec2 create-tags」コマンドを実行します。
セキュリティグループにタグを付ける
「aws ec2 create-tags」コマンドでセキュリティグループにタグを付けることができます。
■コマンド
|
aws ec2 create-tags –resources `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tags Key=Name,Value=Test-EC2-Instance-001-sg |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 create-tags –resources `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tags Key=Name,Value=Test-EC2-Instance-001-sg |
■AWS 管理画面での確認
実行前
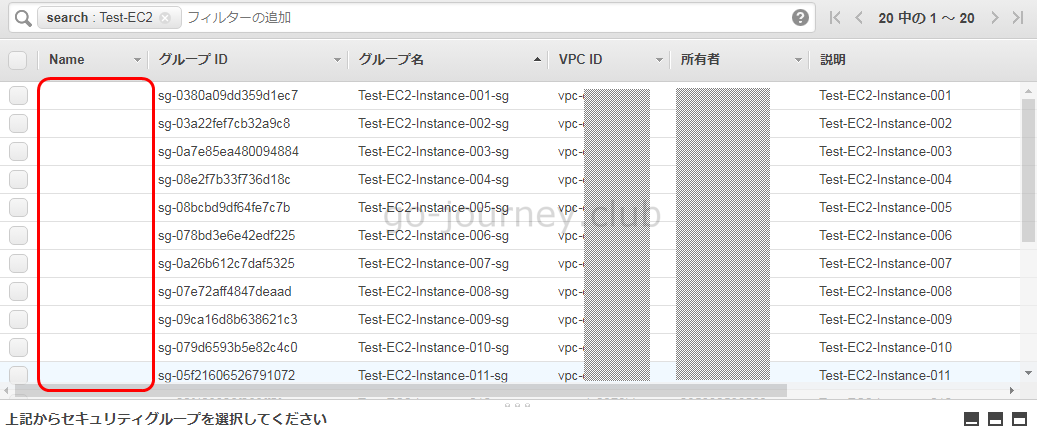
実行後
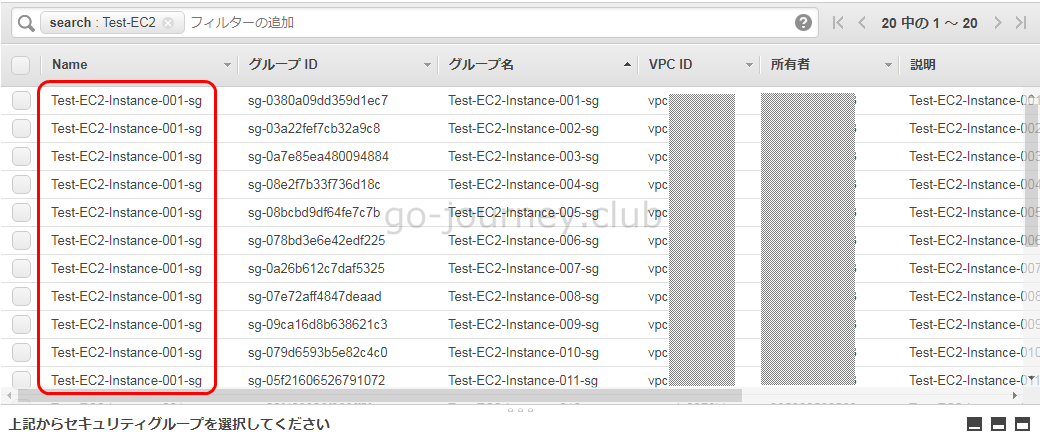
An error occurred (UnauthorizedOperation) when calling the CreateSecurityGroup operation: You are not authorized to perform this operation.
権限が足りない場合は以下のような「You are not authorized to perform this operation.」のメッセージが出力されます。
|
[test@RedHat8 ~]$ aws ec2 create-security-group –group-name Test-EC2-Instance-001-sg –vpc-id vpc-xxxxxxx –description “Test-EC2-Instance-001-sg”
An error occurred (UnauthorizedOperation) when calling the CreateSecurityGroup operation: You are not authorized to perform this operation. |
【トピック】大量にコマンドを実行した際にエラーになる場合
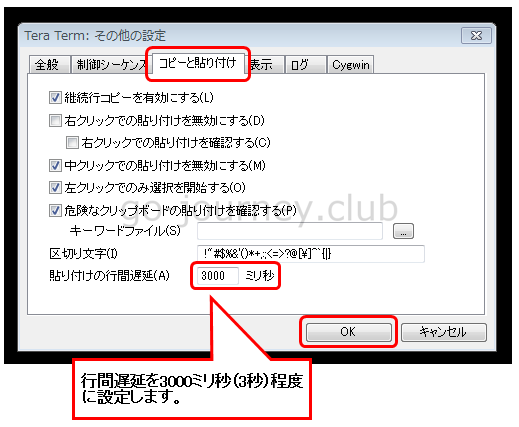
AWS CLI コマンドを数十行、数百行レベルで実行する際にエラーになる場合があります。
その場合はコマンドの投入が速すぎるのでコマンド投入のタイミングを遅らせます。
TeraTerm の場合は以下の設定をします。
メニューより「設定」をクリックします。
「その他の設定」をクリックします。
「コピーと貼り付け」タブで「貼り付けの行間遅延」を「3000ミリ秒(3秒)」程度に設定し「OK」ボタンをクリックします。
※環境によって異なると思いますが、私の環境で何度も繰り返し行った結果、2~3秒くらいから安定してコマンドを処理できるようになりました。
セキュリティグループを大量に削除する
先ほど作成した大量のセキュリティグループを削除する手順です。
AWS CLI を利用すると何度も作ったり消したりして少しずつ改善ができるので品質を向上させることができます。
「–group-id」でグループIDを引数に取りますが、何度も作ったり消したりする前提なのでIDは都度変わります。
そのため、変わらないグループ名からグループIDを出力して「–grouop-id」の引数にしています。
グループ名からグループIDを出力するコマンドは「`aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r`」の部分です。
最後に「-r」が入っていますが、「-r」を入れないと以下のように「”(ダブルクォーテーション)」で囲まれて出力されます。
■-rオプションがない場合
|
[ec2-user@RedHat8 ~]$ aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ “sg-xxxxxxxx” ← ダブルクォーテーションで囲まれて表示されます。 [ec2-user@RedHat8 ~]$ |
■-rオプションがある場合
|
[ec2-user@RedHat8 ~]$ aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r sg-xxxxxxxxxx ← ダブルクォーテーションがない状態で表示されます。 [ec2-user@RedHat8 ~]$ |
■コマンド
|
aws ec2 delete-security-group –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` |
■コマンド実行結果
コマンド結果は以下のように返り値はありません。
|
[ec2-user@RedHat8 ~]$ aws ec2 delete-security-group –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` |
AWS 管理画面での確認
セキュリティグループにルールを追加する(インバウンド、authorize-security-group-ingress)
セキュリティグループを作成したらインバウンドルールを追加します。
Windows版とLinux版を作成します。
- Windows版 ← 3389/TCP と ICMP(Ping)のみ許可します。
- Linux版 ← 22/TCP と ICMP(Ping)のみ許可します。
※必要な場合は適宜追加します。
■ルールを複数設定する場合
ルールを複数設定する場合は以下のように「–ip-permissions」の後の「IpProtocol~」のひとかたまりずつ入れていきます。
2つ目は半角スペースを空けて「IpProtocol~」以降を入れていきます。
|
–ip-permissions IpProtocol=tcp,FromPort=3389,ToPort=3389,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ IpProtocol=icmp,FromPort=-1,ToPort=-1,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ |
Windows版(インバウンドルール)
■コマンド
|
aws ec2 authorize-security-group-ingress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=3389,ToPort=3389,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ IpProtocol=icmp,FromPort=-1,ToPort=-1,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ |
■コマンド実行結果
返り値はありません。
|
[ec2-user@RedHat8 ~]$ aws ec2 authorize-security-group-ingress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=3389,ToPort=3389,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ IpProtocol=icmp,FromPort=-1,ToPort=-1,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ |
AWS 管理画面の確認
以下のように 1コマンドで複数のルールが作成されていることが確認できます。
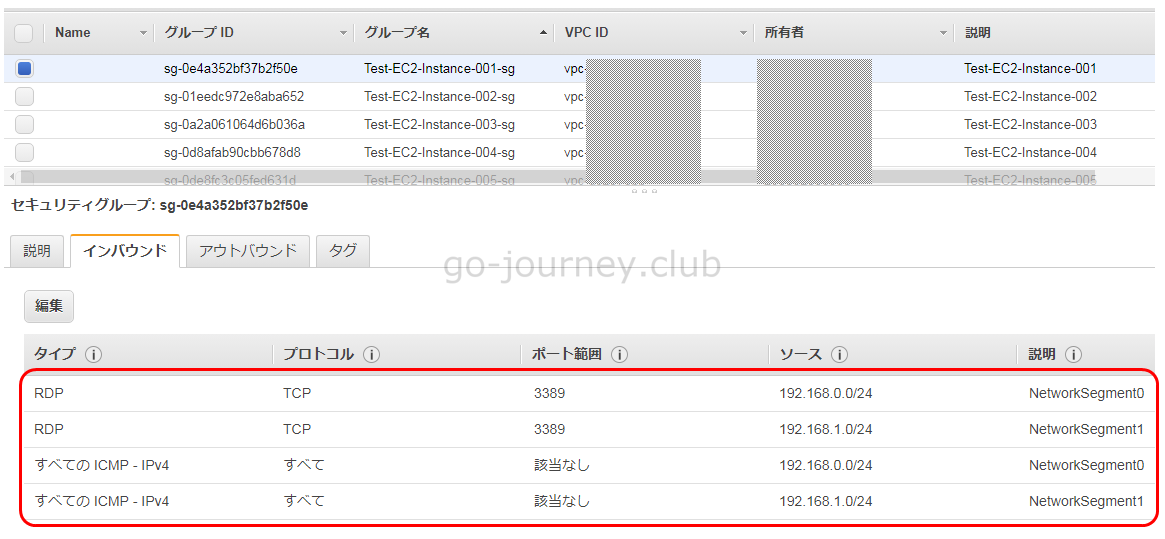
Linux版(インバウンドルール)
■コマンド
|
aws ec2 authorize-security-group-ingress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=22,ToPort=22,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ IpProtocol=icmp,FromPort=-1,ToPort=-1,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 authorize-security-group-ingress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=22,ToPort=22,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ IpProtocol=icmp,FromPort=-1,ToPort=-1,IpRanges='[{CidrIp=192.168.0.0/24,Description=”NetworkSegment0″},{CidrIp=192.168.1.0/24,Description=”NetworkSegment1″}]’ |
AWS 管理画面の確認
以下のように 1コマンドで複数のルールが作成されていることが確認できます。
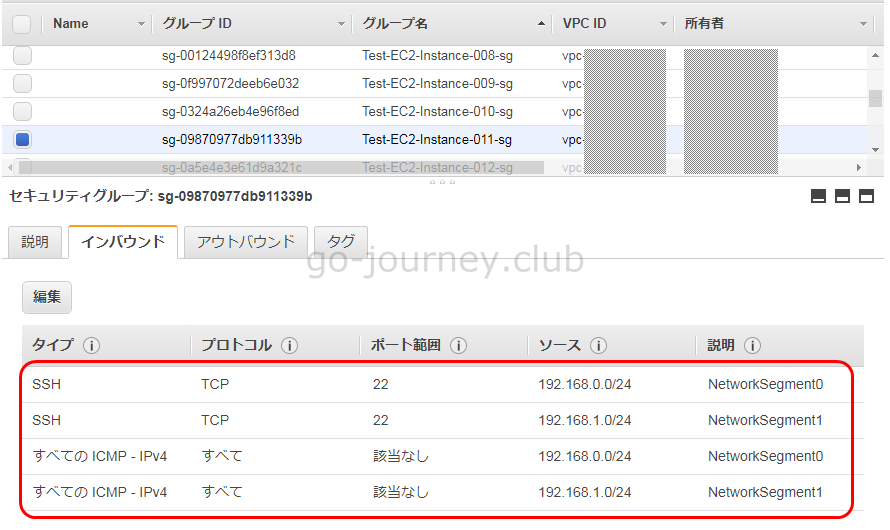
セキュリティグループにルールを追加する(アウトバウンド、authorize-security-group-egress)
次にアウトバウンドにもルールを設定したい場合は以下のコマンドで追加します。
デフォルトではアウトバウンドに関しては全て許可の設定になっています。
ちなみに今回はアウトバウンドのルールで PostgreSQL に接続することを想定し、5432/TCP のみ許可する設定とします。
Windows版(アウトバウンドルール)
■コマンド
|
aws ec2 authorize-security-group-egress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=5432,ToPort=5432,IpRanges='[{CidrIp=10.0.0.0/24,Description=”PostgreSQL Port 5432″},{CidrIp=10.0.1.0/24,Description=”PostgreSQL Port 5432″}]’ |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 authorize-security-group-egress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=5432,ToPort=5432,IpRanges='[{CidrIp=10.0.0.0/24,Description=”PostgreSQL Port 5432″},{CidrIp=10.0.1.0/24,Description=”PostgreSQL Port 5432″}]’ |
AWS 管理画面の確認
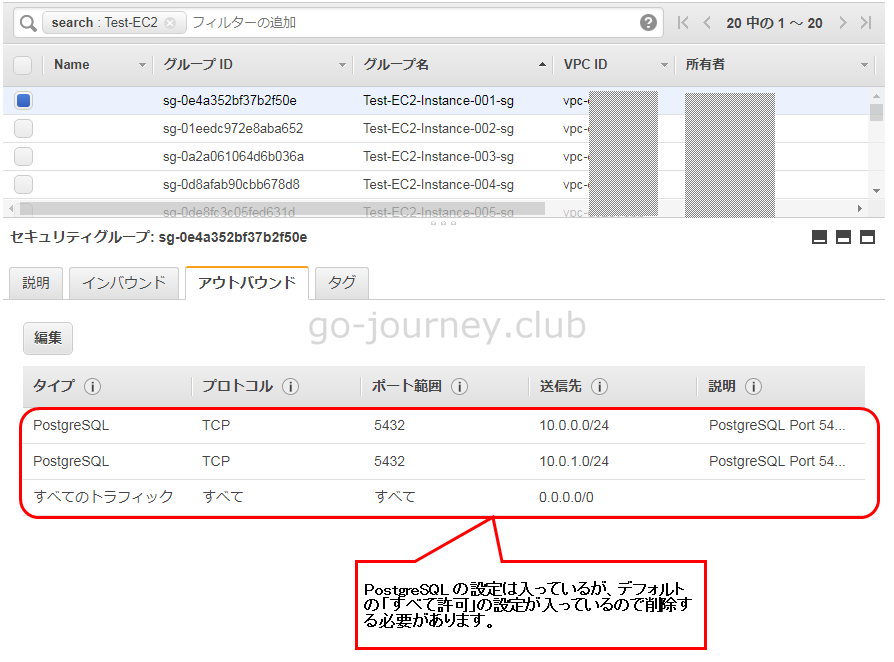
Linux版(インバウンドルール)
※アウトバウンドの場合は、Windows & Linux 同じ設定になりますが、分けて記載しています。
■コマンド
|
aws ec2 authorize-security-group-egress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=5432,ToPort=5432,IpRanges='[{CidrIp=10.0.0.0/24,Description=”PostgreSQL Port 5432″},{CidrIp=10.0.1.0/24,Description=”PostgreSQL Port 5432″}]’ |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 authorize-security-group-egress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –ip-permissions IpProtocol=tcp,FromPort=5432,ToPort=5432,IpRanges='[{CidrIp=10.0.0.0/24,Description=”PostgreSQL Port 5432″},{CidrIp=10.0.1.0/24,Description=”PostgreSQL Port 5432″}]’ |
AWS 管理画面の確認
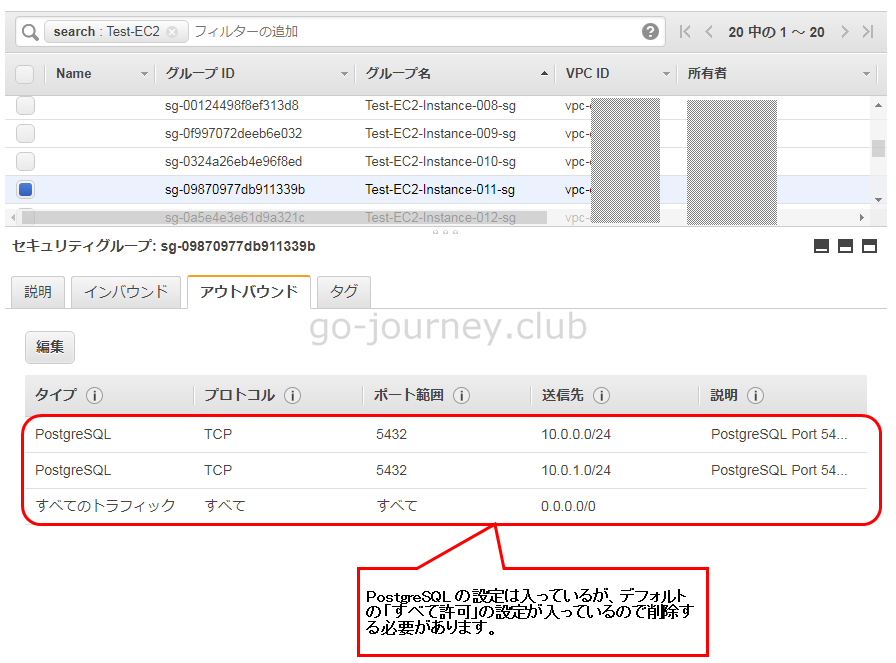
アウトバウンド全て許可の設定を削除する(アウトバウンドを設定した場合に必要)
先ほどアウトバウンドの設定を入れましたが、デフォルトの「全て許可」の設定が残っていました。
そのデフォルトの設定を削除します。
Windows と Linux で同じコマンドになるので一括してコマンドを実行しています。
■コマンド
|
aws ec2 revoke-security-group-egress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –cidr 0.0.0.0/0 –protocol -1 –port -1 |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 revoke-security-group-egress –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –cidr 0.0.0.0/0 –protocol -1 –port -1 |
AWS 管理画面の確認
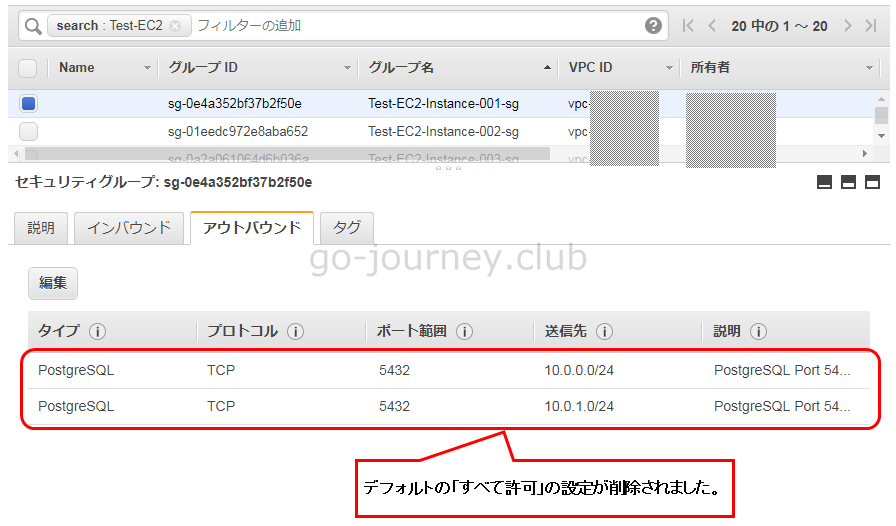
セキュリティグループの内容を確認するコマンド
■コマンド
|
aws ec2 describe-security-groups –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –output table |
■コマンド実行結果
※非常に長くなるため最初の2つのコマンドだけ記載しています。
|
[ec2-user@RedHat8 ~]$ aws ec2 describe-security-groups –group-id `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –output table |
セキュリティグループ名とセキュリティグループIDの確認方法
今回はセキュリティグループIDを使用する機会がありませんでしたが、以下のコマンドでセキュリティグループ名とセキュリティグループIDを確認できます。
■アウトプットがtableの場合
|
[ec2-user@RedHat8 ~]$ aws ec2 describe-security-groups –query “SecurityGroups[].[GroupName,GroupId]” –output table |
■アウトプットがtextの場合
|
[ec2-user@RedHat8 ~]$ aws ec2 describe-security-groups –query “SecurityGroups[].[GroupName,GroupId]” –output text |
■アウトプットがデフォルト(json)の場合
|
[ec2-user@RedHat8 ~]$ aws ec2 describe-security-groups –query “SecurityGroups[].[GroupName,GroupId]” |
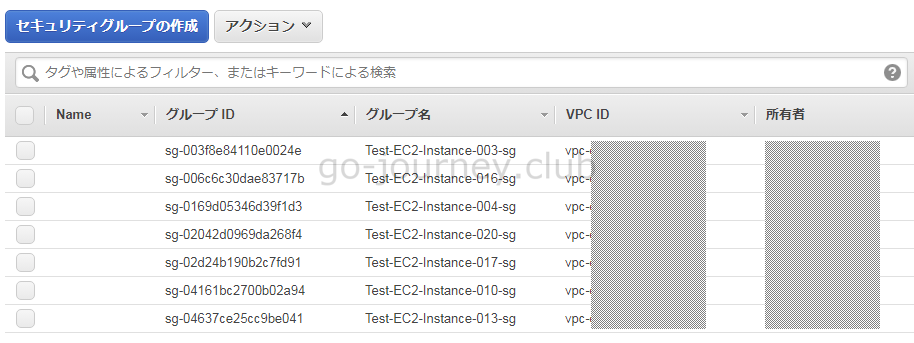
AMI、セキュリティグループを指定して EC2 インスタンスを作成する
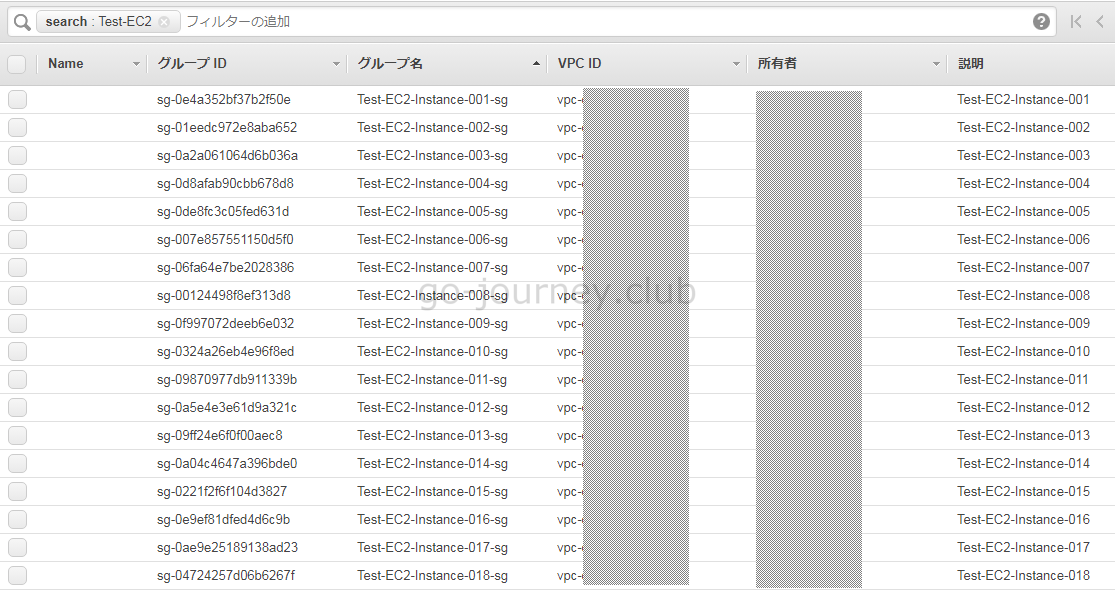
セキュリティグループを20個分作成したので EC2 インスタンスを作成し、1つ1つのインスタンスに対してセキュリティグループを1つずつ割り当てます。
セキュリティグループをまとめてもいいのですが、まとめるとセキュリティグループを変更する際に影響範囲を正確に把握することが難しくなり思わぬ事故を引き起こしてしまう可能性があります。
せっかくコマンドラインから AWS を操作できるようになったため、1インスタンスに 1セキュリティグループを割り当てても手間ではありません。
AMI を決定する
まずは AMI を決定します。
Linux の場合は RedHat 系、Windows の場合は Windows の AMI を選択します。
今回は以下のようにしました。
- Windows ← ami-0404c1383f6b870a2
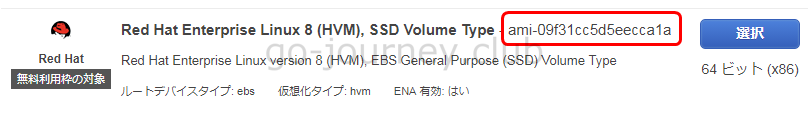
- Linux ← ami-09f31cc5d5eecca1a
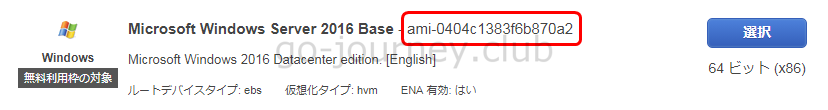
■Windows
Microsoft Windows Server 2016 Base – ami-0404c1383f6b870a2
Microsoft Windows 2016 Datacenter edition. [English]
■Linux
Red Hat Enterprise Linux 8 (HVM), SSD Volume Type – ami-09f31cc5d5eecca1a
Red Hat Enterprise Linux version 8 (HVM), EBS General Purpose (SSD) Volume Type
Windows版(dry-run付き)
■コマンド
|
aws ec2 run-instances –dry-run –region ap-northeast-1 –image-id ami-0404c1383f6b870a2 –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.101 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-001}]’ –output table |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 run-instances –dry-run –region ap-northeast-1 –image-id ami-0404c1383f6b870a2 –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.101 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-001}]’ –output table |
AWS 管理画面の確認
dry-run なので AWS 管理画面には何も反映されません。
Linux版(dry-run付き)
■コマンド
|
aws ec2 run-instances –dry-run –region ap-northeast-1 –image-id ami-09f31cc5d5eecca1a –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.111 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-011}]’ –output table |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 run-instances –dry-run –region ap-northeast-1 –image-id ami-09f31cc5d5eecca1a –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.111 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-011}]’ –output table |
AWS 管理画面の確認
dry-run なので AWS 管理画面には何も反映されません。
次に dry-run オプションを外して実際に作成します。
Windows版(実際に作成する)
■コマンド
|
aws ec2 run-instances –region ap-northeast-1 –image-id ami-0404c1383f6b870a2 –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.101 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-001}]’ –output table |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 run-instances –region ap-northeast-1 –image-id ami-0404c1383f6b870a2 –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.101 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-001-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-001}]’ –output table |
AWS 管理画面の確認
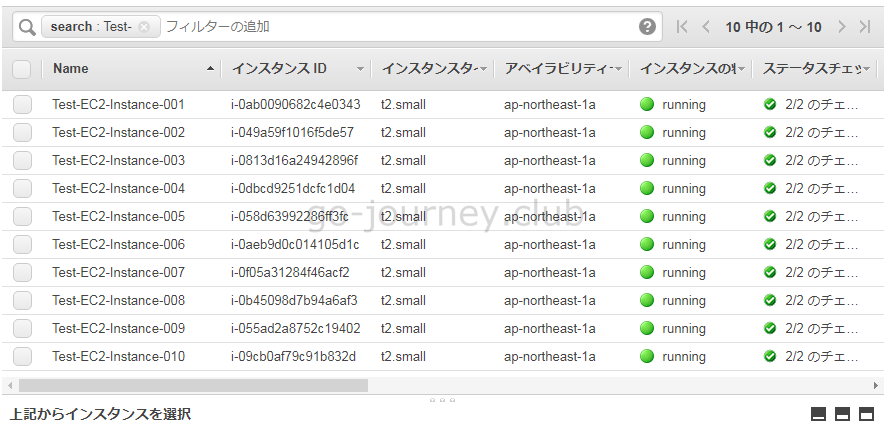
Linux版(実際に作成する)
■コマンド
|
aws ec2 run-instances –region ap-northeast-1 –image-id ami-09f31cc5d5eecca1a –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.111 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-011}]’ –output table |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 run-instances –region ap-northeast-1 –image-id ami-09f31cc5d5eecca1a –count 1 –instance-type t2.small –key-name basic-network –subnet-id subnet-653b2a2c –private-ip-address 172.31.32.111 –security-group-ids `aws ec2 describe-security-groups –filters “Name=group-name,Values=Test-EC2-Instance-011-sg” | jq ‘.SecurityGroups[].GroupId’ -r` –tag-specifications ‘ResourceType=instance,Tags=[{Key=Name,Value=Test-EC2-Instance-011}]’ –output table |
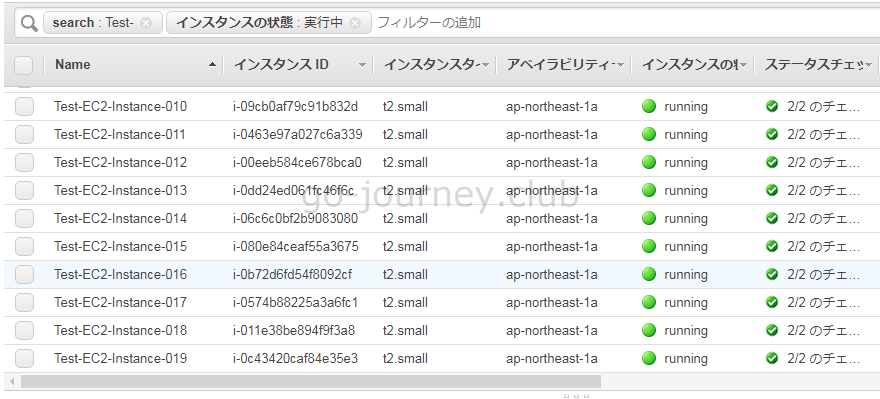
最後の1つが制限に引っかかってしまいました。
確認すると「t2.small」は「20」個までしか作成できないように制限されていました。
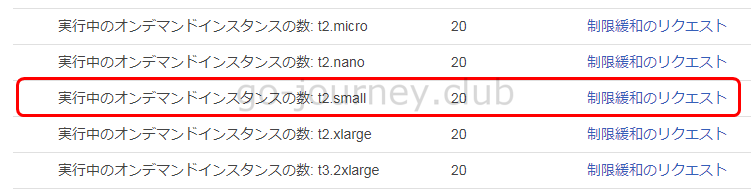
AWS 管理画面の確認
【確認】インスタンスの Name タグよりインスタンスIDを取得する
■コマンド
|
aws ec2 describe-instances –filter “Name=tag:Name,Values=Test-EC2-Instance-001″| jq ‘.Reservations[].Instances[].InstanceId’ -r |
■コマンド実行結果(削除中のインスタンスも表示される)
|
[ec2-user@RedHat8 ~]$ aws ec2 describe-instances –filter “Name=tag:Name,Values=Test-EC2-Instance-001″| jq ‘.Reservations[].Instances[].InstanceId’ -r |
削除中のインスタンスは表示しない(起動中、running のみ表示する)ためには filter に「”Name=instance-state-name,Values=running”」を追加します。
■コマンド(削除中のインスタンスは表示しない)
|
aws ec2 stop-instances –instance-ids `aws ec2 describe-instances –filter “Name=tag:Name,Values=Test-EC2-Instance-001” “Name=instance-state-name,Values=running”| jq ‘.Reservations[].Instances[].InstanceId’ -r` |
■コマンド実行結果(削除中のインスタンスは表示しない)
|
[ec2-user@RedHat8 ~]$ aws ec2 stop-instances –instance-ids `aws ec2 describe-instances –filter “Name=tag:Name,Values=Test-EC2-Instance-001” “Name=instance-state-name,Values=running”| jq ‘.Reservations[].Instances[].InstanceId’ -r` |
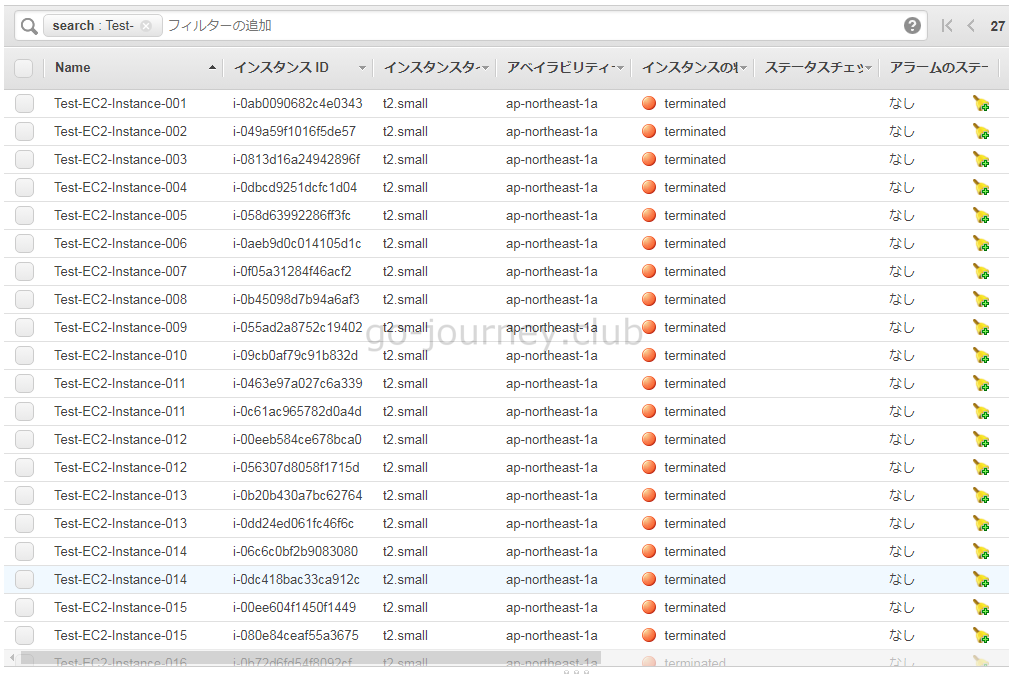
作成した EC2 インスタンスを削除する
最後に作成した EC2 インスタンスを削除します。
■コマンド
|
aws ec2 terminate-instances –instance-ids `aws ec2 describe-instances –filter “Name=tag:Name,Values=Test-EC2-Instance-001″| jq ‘.Reservations[].Instances[].InstanceId’ -r` |
■コマンド実行結果
|
[ec2-user@RedHat8 ~]$ aws ec2 terminate-instances –instance-ids `aws ec2 describe-instances –filter “Name=tag:Name,Values=Test-EC2-Instance-001″| jq ‘.Reservations[].Instances[].InstanceId’ -r` |
AWS 管理画面での確認



コメント